Vessel Impersonation Cyber Report March 2020 Week Four
Georgios Papaioannou - CEO & co founder at Crontab Cyber Security Limited
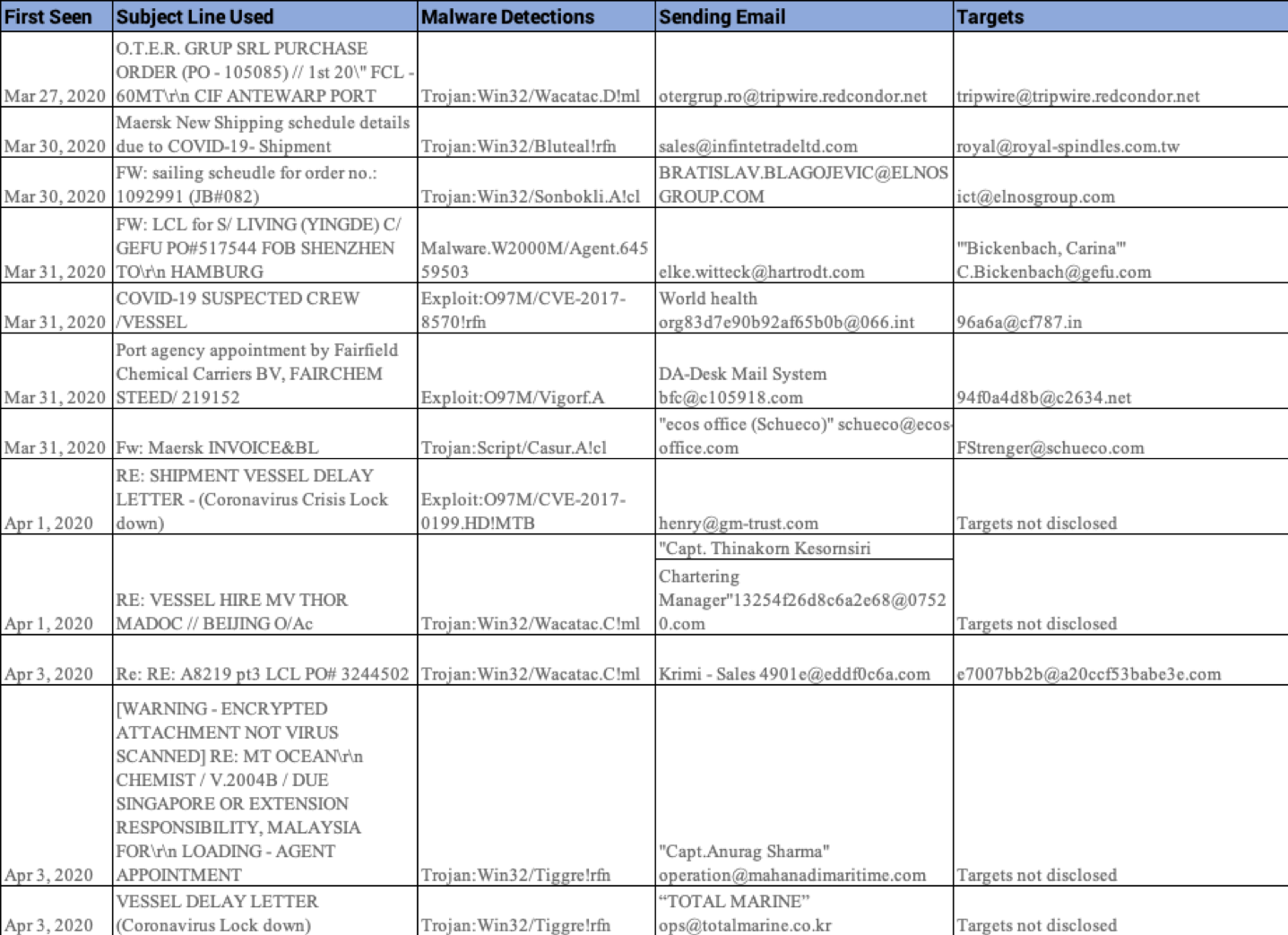
In the above collection we see malicious actors attempting to use vessel names to try to spoof companies in the maritime supply chain. This week we observed a large percentage of these malicious emails attempting to deliver Windows trojan malware. Some of the new Vessel names used this week include "MV THOR MADOC" which and we see "MT Ocean Chemist" again this week among others.
An email was observed attempting to impersonate a "Maersk" employee using a subject line of "Maersk New Shipping schedule details due to COVID-19- Shipment notification." The sender includes "Maersk" and "COVID-19" in the subject line to trigger the recipient to believe the message is urgent and related to the current CoronaVirus Pandemic.
Analysis reveals that the malicious email was sent from an illegitimate domain - infintetradeltd[.]com. The text content of the website infintetradeltd[.]com is "codermails[.]in, Bulk Automated Mailing Server Installer codermails[.]in Bulk Emailing Made Easy!" which further indicates its illegitimacy. Impersonating Maersk is a common tactic and Red Sky Alliance has seen a significant increase in malicious emails related to the current COVID-19 Pandemic.